Log into your Kali VM. sudo is commonly used to control privileged commands on Linux. One can list the privileges your account has by running the command below:
sudo -lAnswer the following question:
- What do your privileges allow you to do when running
sudo?
When configuring a machine with multiple administrators, one typically sets up a sudoers group and includes each administrator in the group. That group is then configured with privileges to perform commands via sudo. Run the groups command to find out the groups your account belongs to.
groupsAnswer the following question:
- What is the name of the
sudoersgroup your account is a part of?
Examine the file /etc/sudoers to view the accounts that have access to sudo and their privileges. Note that you will need to use sudo to perform the command since the file's permissions do not allow read access otherwise.
sudo cat /etc/sudoersAt the end of this file, a directive @includedir is used to add configuration information from a directory. Visit this directory and find the file that configures the sudo privileges for the sudoers group you are in.
- Take a screenshot of its contents that includes your OdinId
A misconfigured sudoers file can allow a non-privileged account to escalate their privileges to the root user. One of the accounts that has been misconfigured is the guest account. Revisit the /etc/sudoers file and find the entry that configures the guest account's access to the sudo command.
- What do the
guestaccount's privileges allow it to do when runningsudo?
Switch from your account to the guest account by either using the login information obtained from the previous labs or via sudo and su (switch user):
sudo su - guestThen, run the command to list your privileges to show they match what's in the /etc/sudoers file.
sudo -lGTFOBins

GTFOBins is a curated list of binaries that can be used to perform privilege escalation as a result of misconfigured systems. Visit the site and lookup the binary that the guest account has been given sudo access to run. Answer the following question:
- What command will allow you to execute a shell using the binary listed?
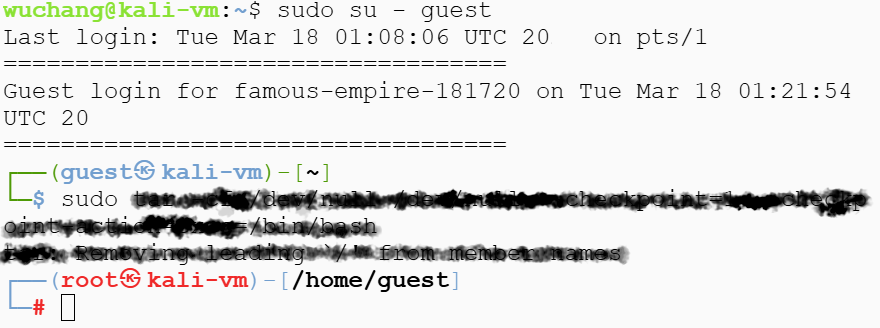
Run the command using sudo to spawn a root shell using /bin/bash.
- Take a screenshot of the execution of commands that result in a root shell that includes your OdinID


Join the following room on TryHackMe: https://tryhackme.com/room/linuxprivesc. The room covers the use of user-defined functions to exploit a MySQL server running as root, password tampering, exploiting vulnerable SUID binaries and scripts, PATH hijacking, and credential compromises. Complete the exercise, but skip Tasks 10, 13, 14, 15, and 19.
Note that for Task 3, you will need to copy and paste the password hash found for the root user into the course's Kali VM.
hash.txt
$6$Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET..it8r.jbrlpfZeMdwD3B0fGxJI0
Then, run the hash through the John the Ripper tool against the rockyou.txt file on the VM.
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
- Take a screenshot showing completion of the other tasks in the room


Join the following room on TryHackMe: https://tryhackme.com/room/kenobi. The room covers a common set of tactics that adversaries follow when they have access on a victim's network: scanning for network file system shares and copying files from those with misconfigured permissions.
- Take a screenshot showing completion of the room