The goal of this final project is to reverse-engineer a piece of recent malware using everything you have learned in this course. After doing so, you will create a narrated screencast that walks-through your process of obtaining the malware, running the analysis on it, and analyzing its behavior.
For Windows-based malware, you may use our institution's academic account to download copies of recent versions of the operating system. Follow the instructions at this link: https://cat.pdx.edu/services/software/users/microsoft-software/ . You may also use Microsoft Edge Developer to download Virtual Machines for testing: https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/. After installation, you may perform the analysis on equivalent static and dynamic analysis tools.
To find resources for malware to analyze, visit the links below:
- VirusTotal
- Daily Dose of Malware script
- Malware Bazaar Database (SolarWinds sample)
- MalShare (SolarWinds sample)
- awesome malware analysis
- theZoo (SolarWinds sample)
- Virus Underground
Other examples of recent malware you may attempt to track down and reverse engineer include
After completing your analysis, you will then create a narrated screencast no longer than 15 minutes in length that walks-through the malware you reverse-engineered. To ensure you are the one completing the screencast, your screencast MUST initially include a video of you narrating the walkthrough. It is recommended for you to record your screencast as a recorded screen share on Zoom. Note that, when logged into Zoom, recordings are automatically captured and uploaded to PSU's Media Space and can be accessed after a short time by visiting "My Media" within Media Space.
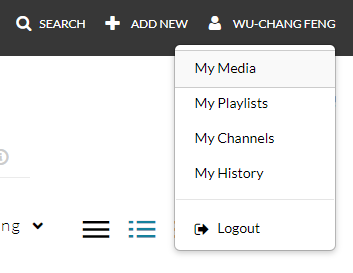
Alternatively, you may also record your screencast using the software on Media Space (e.g. Kaltura Capture) or from tools such as QuickTime or Open Broadcaster. You will then upload your screencast via PSU's Media Space by visiting the site and clicking on "My Media".
After selecting and uploading the video, you will then bring the video up on Media Space, select the "Publish" tab, click on "Unlisted", and then "Save".
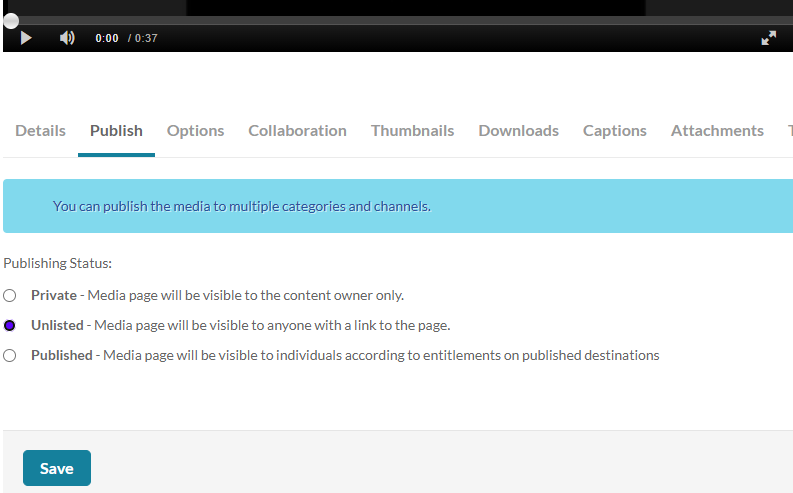
Then, retrieve the screencast's URL from MediaSpace. Submit the URL in Canvas under the "Final Project" assignment.
We will be using the following rubric to evaluate your project.
|
|
|
|
|